Dark Web Hacker and How to Hire One Safely
If you want to hire a dark web hacker, it is imperative that you stay anonymous. You have to ensure each step you take is secured, hiding your location and personal details. You want to ensure you use communication media that is known to be safe and anonymous such as Wickr app, telegram, Signal, proton mail and so on.
Since the idea is to stay anonymous every step of the way, this will mean when making payment, you will have to use a payment method that ensures you are secured. Never use traditional payment methods such as bank transfer, Paypal, cash app to pay a hacker. The best payment methods used on the dark web is crypto currency. Crypto is the best option for anyone trying to stay anonymous when making payment online.
Dark Web Hacker Services for Hire
-
Rated 5.00 out of 5 based on 15 customer ratings$3,000.00
-
-
-
Rated 5.00 out of 5 based on 8 customer ratings$500.00 – $800.00
-
-
-
Rated 4.85 out of 5 based on 13 customer ratings$300.00
How to Contact a Dark Web Hacker
If you are looking to contact a dark web hacker, then you are in the right place. We offer dark web services as hackers that can help you achieve a lot of things. You can contact us through any of the following: Telegram/Signal: +1 (619) 693 7813, Wickr: hackerforhire and Email: professionalhackerforhire@protonmail.com

How to Access the Dark Web
What is the dark web?
When people go on about the so-called dark web, they’re usually talking about onion sites, which aren’t searchable via Google or accessible via standard browsers. On the regular web, domains such as www.wired.co.uk are translated into their actual IP addresses via the domain name system (DNS).
“The whole point of onion addresses – ‘the dark web’, ‘the silk road’ — is that they throw all this stuff away, and with it they dispose of the opportunities for censorship,” says Alec Muffett, a security engineer who’s on the board at the Open Rights Group and has built onion sites for Facebook and The New York Times.
“The Tor network is another network which sits on top of the TCP/IP internet, stitching the participating computers together into a wholly new network ‘space’, not IPv4, not IPv6, but ‘Onion Space’.” In other to access onion sites you need the Tor Browser
What is Tor?
When you use the Tor network, your traffic is layered in encryption and routed via a random relay, where it’s wrapped in another layer of encryption. That’s done three times across a decentralized network of nodes called a circuit , the nodes are run by privacy-focused volunteers; thanks, you lovely people making it difficult to track you or for sites to see where you’re actually located.
Alongside bouncing encrypted traffic through random nodes, the Tor browser deletes your browsing history and cleans up cookies after each session. But it has other clever tricks to push back against trackers. If someone visits two different sites that use the same tracking system, they’d normally be followed across both. The Tor browser spots such surveillance and opens each via a different circuit making the connections look like two different people, so the websites can’t link the activity or identity if they login on one of the sites.
How to download and use Tor Browser
It’s almost embarrassingly easy thanks to the Tor Browser. Based on Mozilla’s Firefox, this browser hides all that pinging about in the background. “It’s a web browser. Use it like one. It’s that simple,” says Muffett. That’s the desktop edition, but there’s a version for Android and an unsupported onion browsing app for iOS.
While some can simply install and use the Tor browser like any other, there are a few complications for those in countries where Tor is blocked, on corporate or university networks where it’s banned, or where more security is needed. When you start a session, you’ll be shown an option to Connect or Configure.
The latter choice is for when access to the Tor network is blocked, and you’ll be shown a variety of circumvention techniques. Those include traffic obfuscation tools called pluggable transports, which make it look like Tor traffic is random or going to major websites such as Amazon, rather than connecting to the onion network. If you’re having trouble connecting to the Tor network, try one of these.
There are different levels of security in the browser that are worth considering. To review security settings, click on the onion logo in the top left and select “Security Settings”, which will bring up a slider offering a choice of the default of standard, or safer and safest. In “safer” mode, JavaScript is disabled on HTTP sites, some fonts are disabled, and all audio and video won’t run automatically, you’ll have to click to play. Slide up to the “safest” level, and as well as those settings, JavaScript is disabled on all sites.
Once you’ve downloaded and installed the Tor browser, you can browse just as you would your usual browser, but Muffett offers a caveat to avoid unencrypted sites — those with only “http” in the URL rather than “HTTPS”. He notes: “This is because plain old HTTP traffic can be tampered with.” Handily, the Tor Browser comes with the HTTPS Everywhere add-on installed by default, which forces a site to serve the secure version if one is available.
How to access the dark web using Tor
Using the Tor browser is simple, but knowing when to fire it up is more complicated. You could do all your browsing with Tor, though it’s slower than a standard browser, something the Tor Project is working hard at to improve, says Stephanie Whited, communications director for the Tor Project. Another challenge is CAPTCHAs; because Tor behaves differently than other browsers, it’s more likely to trigger the bot-hunting system, so be prepared to face more of them than usual.
Whited’s rule of thumb is to use the Tor Browser instead of Private Browsing Mode or Incognito Mode. “Contrary to what most people think, these modes do not actually protect your privacy,” she says. “They do not curtail the collection of your online activity by your ISP, advertisers, and trackers. They don’t prevent someone monitoring your network from seeing what websites you’re visiting. Tor Browser does.”
With any security and privacy issue, it’s about your threat model, which is simply what attacks or invasions you’re actually worried about. “When you want to visit a site and for nobody in-between you and the site to know that you are visiting it,” says Muffett, about when to use the Tor Browser. “Sure, most people think ‘porn’ when someone says that, but it also applies to getting some privacy when you want not to be immediately traceable: sexual health, birth control questions, foreign news, personal identity questions.”
But there’s more to Tor than being nearly anonymous online. “The big win of Tor for me is access — with a sprinkling of anonymity, to be sure — but that I can be stuck behind some hotel firewall, in some airport or restaurant lounge, or in a sketchy cafe is a sketchy country,” Muffett says. “And if I use Tor then I have a good degree of certainty that at least the local weirdos are not looking over my digital shoulder at what I am browsing — and that when I kill my browser (unless I’ve bookmarked something, or saved a file) then all the data is properly cleaned-up and wiped.”
VPNs are often recommended as protection in such cases, but Whited disagrees. “VPNs can be a security bottleneck,” she says. “All of your traffic goes through it, and you have to trust them as if they are your new ISP. Because the backbone of our software is a decentralized network, you don’t have to trust us to browse the internet privately.”
Why Hire a Dark Web Hacker
With over 3598 successfully-completed projects and numerous happy clients who have solicited our hacking services, our team of professional hackers is known to many as undoubtedly one of the team of hackers who happen to be on top of their game in the hacking community.
Professional Hacker for Hire is known to take good care of clients as well as their projects seriously with a guaranteed claim their task will be completed and on time. The team makes this claim because, we only accept tasks we are able to complete with no doubts.
Where to Hire a Dark Web Hacker
The best place to get a hacker a for hire is at professional hacker for hire website. We are a team of Professional Penetration Testers, Security Experts and an Ethical Hackers offering Hacking Services online on the Dark Web and Clear net. you can contact us to negotiate prices or hire us.
Pricing for Dark Web Hacker Services
One of our greatest organization goals is keeping our customers satisfied by offering them mouth-watering prices. Prices for hacking services at Professional Hacker for Hire are relative cheap and are completely negotiable.
Prices are relative lower thanks to the length of time we have been in business. Team members have the necessary skills and we have acquired most of the tools needed for the common hacks we offer. Contact us now to get good pricing on the hacking services we provide.
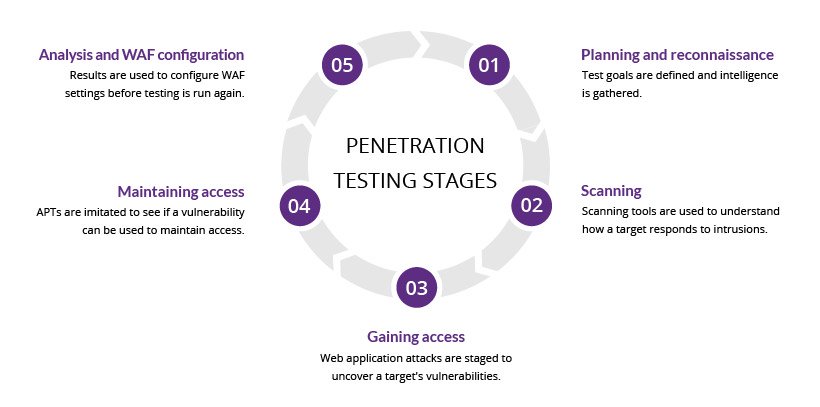
How ever certain services such as social media accounts hacks, account recovery, email hacking have relatively fixed prices. Negotiations are done for heavy tasks such as penetration and testing, mobile phone cloning website hacking and other heavy tasks.
References
There is no good article that doesn’t profit from the knowledge of other blogs and people. We used information from the following sites when we compiled this beautiful peace.